 Chances are you’ve heard of ransomware before- it’s been around for a while. Recently though, ransomware has branched out significantly. Since 2013 there has been a gradual increase in types, and by late 2016, the amount of ransomware seemed to explode, with 10+ new variants per month. This isn’t surprising though. The ransomware business is a multi-billion dollar industry.
I want you to reread that sentence. Ransomware is a BUSINESS. No longer is any kind of hacking one greasy 30 year old living in his moms basement. These are companies with many employees and an office building just like any other business. They have quotas, business plans for the quarter, and meetings just like your business does. Ransomware is even offered as a service with kits you can buy to send out your own ransomware.
Chances are you’ve heard of ransomware before- it’s been around for a while. Recently though, ransomware has branched out significantly. Since 2013 there has been a gradual increase in types, and by late 2016, the amount of ransomware seemed to explode, with 10+ new variants per month. This isn’t surprising though. The ransomware business is a multi-billion dollar industry.
I want you to reread that sentence. Ransomware is a BUSINESS. No longer is any kind of hacking one greasy 30 year old living in his moms basement. These are companies with many employees and an office building just like any other business. They have quotas, business plans for the quarter, and meetings just like your business does. Ransomware is even offered as a service with kits you can buy to send out your own ransomware.
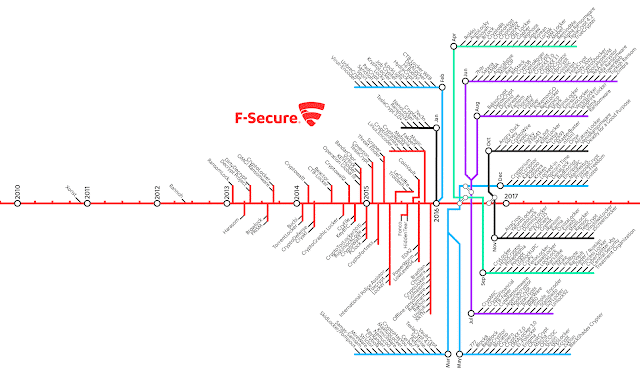 timeline of ransomware spreading from 2000 to 2017
What Is Ransomware?
Ransomware is a form of malware or a virus that prevents users from accessing their systems or data until a sum of money is paid.¹ Typically, targets are home users since their security is weak or nonexistent. What we’re seeing more and more of though, are small businesses being targeted- and being successfully hacked. In fact, small businesses account for the majority of data breaches (58%).²
The appeal of small businesses is the amount of personal data available with a high chance of weak security. Hackers know that the IT budget for SMB’s is lacking and use that to their advantage. They know that these small businesses need their files, data, and client information to stay in business and to stay respected in their industry. Without the budget of a large company for preventative measures, SMB’s pay the ransom and hope that no one finds out.
BLOG: The Value of an MSP to Small Businesses with Small Tech Budgets
Should I Pay the Ransom?
There are varying opinions on if you should pay the ransom or not. It depends on who you ask- different motivations create different options. A business owner would pay it because they need their files. Law enforcement wouldn’t pay it because they want to cut off the hackers money source. A cybersecurity expert would first see if there was a workaround before paying. Unfortunately, one in five companies who pay the ransom don’t get their files back³, so whether you pay or not- it’s risky.
timeline of ransomware spreading from 2000 to 2017
What Is Ransomware?
Ransomware is a form of malware or a virus that prevents users from accessing their systems or data until a sum of money is paid.¹ Typically, targets are home users since their security is weak or nonexistent. What we’re seeing more and more of though, are small businesses being targeted- and being successfully hacked. In fact, small businesses account for the majority of data breaches (58%).²
The appeal of small businesses is the amount of personal data available with a high chance of weak security. Hackers know that the IT budget for SMB’s is lacking and use that to their advantage. They know that these small businesses need their files, data, and client information to stay in business and to stay respected in their industry. Without the budget of a large company for preventative measures, SMB’s pay the ransom and hope that no one finds out.
BLOG: The Value of an MSP to Small Businesses with Small Tech Budgets
Should I Pay the Ransom?
There are varying opinions on if you should pay the ransom or not. It depends on who you ask- different motivations create different options. A business owner would pay it because they need their files. Law enforcement wouldn’t pay it because they want to cut off the hackers money source. A cybersecurity expert would first see if there was a workaround before paying. Unfortunately, one in five companies who pay the ransom don’t get their files back³, so whether you pay or not- it’s risky.
 The FBI does not support paying a ransom to the adversary. Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after having paid a ransom.⁴
How Do I Prevent Ransomware from Affecting Me?
Ransomware is very serious, but preventative measures can keep you and your business from having to suffer. Having a proactive cyber security solution is the best option when dealing with any form of cyber attack.
Patch and update your computer regularly. Patches to your machine don’t get applied until your computer reboots, so make sure to do so to ensure your patches are actually working.
Backup, Backup, Backup! The best defense against a ransomware attack is having a continuous backup of your whole computer somewhere else. That way, you don’t lose anything.
Antivirus is your wingman. Antivirus alerts you when attacks like ransomware are put on your computer.
Don’t install programs you don’t trust. If you’re unsure of who makes the program or what exactly it does, don’t download it.⁵
BLOG: 8 Ways To Keep Your Small Business Secure
Ransomware is guaranteed to happen unless you have some sort of cyber security in place. Having just a good eye on which programs are good or bad to download or just having antivirus won’t be enough. The good news is that patches and some antivirus and backup solutions are little or no cost at all- and will save you hundreds of thousands in damages.
Ransomware is one way that hackers can take advantage of your business, check out these other 5 ways your network can become compromised.
The FBI does not support paying a ransom to the adversary. Paying a ransom does not guarantee an organization will regain access to their data; in fact, some individuals or organizations were never provided with decryption keys after having paid a ransom.⁴
How Do I Prevent Ransomware from Affecting Me?
Ransomware is very serious, but preventative measures can keep you and your business from having to suffer. Having a proactive cyber security solution is the best option when dealing with any form of cyber attack.
Patch and update your computer regularly. Patches to your machine don’t get applied until your computer reboots, so make sure to do so to ensure your patches are actually working.
Backup, Backup, Backup! The best defense against a ransomware attack is having a continuous backup of your whole computer somewhere else. That way, you don’t lose anything.
Antivirus is your wingman. Antivirus alerts you when attacks like ransomware are put on your computer.
Don’t install programs you don’t trust. If you’re unsure of who makes the program or what exactly it does, don’t download it.⁵
BLOG: 8 Ways To Keep Your Small Business Secure
Ransomware is guaranteed to happen unless you have some sort of cyber security in place. Having just a good eye on which programs are good or bad to download or just having antivirus won’t be enough. The good news is that patches and some antivirus and backup solutions are little or no cost at all- and will save you hundreds of thousands in damages.
Ransomware is one way that hackers can take advantage of your business, check out these other 5 ways your network can become compromised.
 ¹https://phoenixnap.com/blog/ransomware-statistics-facts
²https://www.ninjarmm.com/blog/small-business-cybersecurity-statistics-2019/
³https://blog.trendmicro.com/what-happens-when-victims-pay-ransomware-attackers/
⁴https://cybersecurityventures.com/global-ransomware-damage-costs-predicted-to-exceed-8-billion-in-2018/
⁵https://www.csoonline.com/article/3236183/what-is-ransomware-how-it-works-and-how-to-remove-it.html
image: https://labsblog.f-secure.com/2017/04/18/ransomware-timeline-2010-2017/
¹https://phoenixnap.com/blog/ransomware-statistics-facts
²https://www.ninjarmm.com/blog/small-business-cybersecurity-statistics-2019/
³https://blog.trendmicro.com/what-happens-when-victims-pay-ransomware-attackers/
⁴https://cybersecurityventures.com/global-ransomware-damage-costs-predicted-to-exceed-8-billion-in-2018/
⁵https://www.csoonline.com/article/3236183/what-is-ransomware-how-it-works-and-how-to-remove-it.html
image: https://labsblog.f-secure.com/2017/04/18/ransomware-timeline-2010-2017/Information Technology Aligned With Your Business Goals?
Baroan is a complete IT services & IT support company working with organizations in Elmwood Park and across the United States of America.
When it comes to IT services and solutions, you need someone who not only comprehends the IT industry but is also passionate about helping clients achieve long-term growth using proven IT solutions. Guy, in leading our company, is committed to helping clients improve their technology in order to develop a competitive edge in their industries.
At Baroan Technologies, Guy Baroan leads a team of dedicated professionals who are committed to delivering exceptional IT services and solutions. With his extensive expertise and hands-on experience, Guy ensures that clients receive the utmost support and guidance in their IT endeavors. Trust in Baroan Technologies to elevate your business systems and stay ahead in today’s competitive landscape.



